| Submission Procedure |
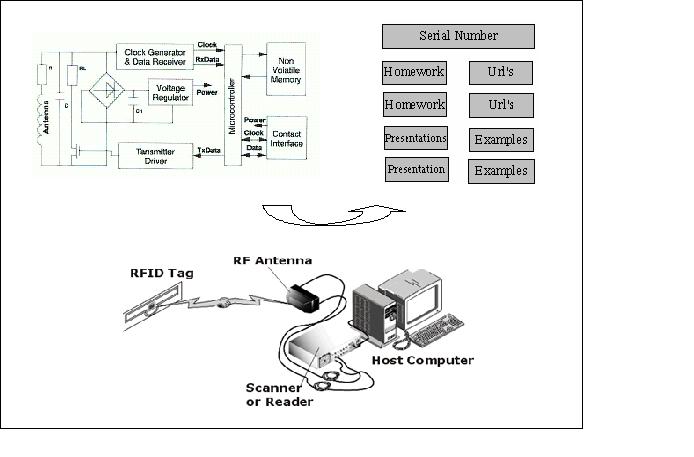
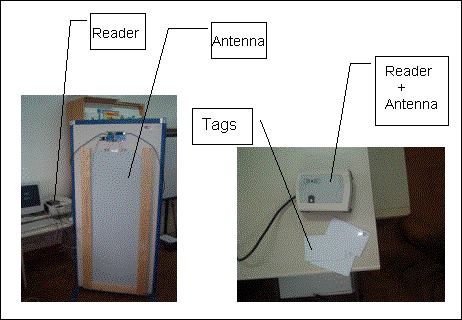
Ubiquitous Computing in the Classroom: An Approach through Identification ProcessJosé Bravo Ramón Hervás Gabriel Chavira Abstract: In recent years, there have been many efforts at research towards obtaining the simple and natural use of computers, with interfaces closer to the user. New visions such as that of the Ubiquitous Computing paradigm emerge. In Ubiquitous Computing the computer is distributed in a series of devices with reduced functionality, spread over the user's environment and communicating wirelessly. With these, context-aware applications are obtained. In this paper we present an approach to the classroom context by identification process using RFID technology, as an implicit input to the system. The main goal is to acquire natural interaction, because the only requirement for the user (teacher or student) is to carry a device (smart label), identifying and obtaining context services. Some of these services and the mechanisms that make them available are described here, together with a scenario of their use in the classroom. Keywords: ubiquitous computing, RFID, implicit interaction, context aware Categories: K.3.1, K.3.2, F.1.2, H.5.2, I.2.6 1 IntroductionFor a large number of people in multiple and diverse environments, computers are tools which are used more and more frequently. Some factors such as price and power have been decisive in their present day, massive-scale use. We are, however, still a long way from making this technology profound and indistinguishable from the setting in which it is embedded. What is really sought is for the user to concentrate on the task rather than on the tool. The Ubiquitous Computing vision [Weiser, 91] proposes the invisible computer and yet at the same time it also advocates its omnipresence, as it approaches users with more intuitive and natural interfaces [Ishii, 97][Harrison, 98]. The main goal is to distribute the computer around the workplace, creating more versatile devices for solving simple processes, using wireless communications- all this as an aide to us in our daily activities. Thus we will transfer computer capabilities to the environment. Page 1494 Research in this field is looking towards user interface models with a continuous presence, showing information at different attention levels, connecting physical and virtual events and seeking the evolution of communication methods. In this paradigm, new forms of interaction are required. In traditional explicit interaction, the user asks the system to carry out the action through sophisticated interfaces. This kind of interaction contradicts the paradigm base of invisible computing. If possible, we need to find more natural interactions without an explicit dialogue of user-computer. Albrecht Schmidt [Schmidt, 00, 05] proposes a definition of Implicit Human Interaction (iHCI): "iHCI is the interaction of a human with the environment and with artefacts which is aimed to accomplish (sic) a goal. Within this process, the system acquires implicit input from the user and may present implicit output to the user" Schmidt defines implicit input as an action recognized and interpreted by the system, but which is not primarily a user action, also affirming that Implicit Output is not directly related to an explicit input and is fully integrated into the context. Finally, Schmidt argues that the system can anticipate the user's needs and provide support. Some efforts are contributing to this paradigm research in the context of education, especially at universities. Weiser proposes the campus as an environment where the benefits of Ubiquitous Computing can be seen most clearly, an environment that places hundred of PCs, Handhelds and many different cards around us, working together with wireless communications and thus making work easier [Weiser, 98]. In the Classroom 2000 Project at Georgia Tech, this paradigm is included in universities in order to facilitate the students' task of listening, synthesizing and understanding what is happening in the classroom, using different devices such as Tablet-PC and boards (Xerox Liveworks LiveBoard) [Abowd, 00]. In this paper our aim is to contribute to this new paradigm with devices situated in the classroom which identify students and teachers. This process allows users to obtain services from the environment with ease. Services such as visualization of teacher presentations or assignments proposed and solved can be obtained. In the next section we present the process of identification by RFID technology. The section following this concentrates on "context" definition and on the fundamental aspects used to analyze our classroom model. Lastly we conclude by focusing on the search for, and adaptation of, new devices to place in the classroom. 2 The identification processPeople identification is an excellent implicit input to the computer. The simple action of walking near the antenna allows the system to read and write information such as Id. Number, profile and other details which can be very useful, depending upon where the users are. Many authors have researched mechanisms for identifying and locating users in organizations. Want and Hopper provided this kind of service by means of active badges, which transmited signals that were picked up by a net of sensors located around the building [Want, 92]. Beigl & Gellersen, in their experiment MediaCups, propose an identification and location process by embedding sensors in everyday objects [Beigl, 01]. Other works focus on certain contexts such as academic conferences. In these the context adapts the information to the user's profile [Cox, 03]. Page 1495 2.1 Radiofrequency Identification (RFID)This technology allows us to identify people and objects easily without any user interaction. Three kinds of objects are clearly differentiated: the reader (reader or transceiver, with an antenna), the label (tag or transponder) and the computer. In Figure 1 we can see the structure of a label in the top left-hand corner. This small device contains a transponder circuit that, in the case of the passive tags, takes the wave energy that the reader continually emits, so as to read and write the information that these may include. The passive tags can store over 512 bytes, including an identification number and other kinds of user information. In this figure, on the right of the label circuit, we can see a distribution of the information, coupled with the teacher and student profiles inside the classroom context. Finally, at the bottom of the figure, the identification devices mentioned previously are shown. RFID technology offers important advantages over traditional bar codes. Some of these advantages are that the labels do not have to be visible to be read, the reader can be located a meter away (with passive tags), they can be reused and the reading speed is over 30 labels per second. In RFID, security is guaranteed. The information is transmitted in an encrypted form and only authorized readers can manipulate the data. Figure 1: Passive tag, distribution of the information and read/write process. Page 1496 This technology is commonly used to identify objects. We consider it an excellent idea to apply it to identifying people, with the added advantage of being able to use the small, dynamic information stored in the tags as a context interaction. Therefore, by identifying people and objects using the same components, a saving of readers and antennas is achieved. Services are thereby increased when new needs appear. Figure 2 shows two types of devices. The one on the left presents a reader and an antenna with read-and-write capability reach of over 75 cm. This has been especially designed for its location on classroom doors or near boards. It can read several labels, simultaneously identifying people entering the classroom. It can also identify the teacher or the students approaching the board. The one on the right is a contact reader including an antenna with a reach of only 10 cm. A model of the tag is also shown. This identification system is especially appropriate for individual use. Figure 2: RFID devices 3 The contextThis concept is an important source of information, but at the present time we have a poor understanding of the wealth that it contains. The power of language, along with the understanding of how the world works and the implicit knowledge of everyday situations, all allow humans to express their ideas well and to communicate with others in an orally-correct manner. The computer-human dialogue does not happen like this; we have more complicated mechanisms of interaction. Many studies and definitions of the term "context" exist. Brooks considers several aspects that we shall now mention as being important: [Brooks, 03] Page 1497
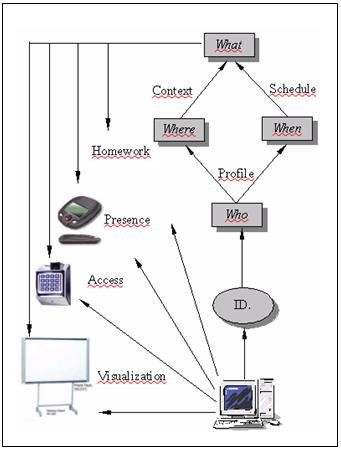
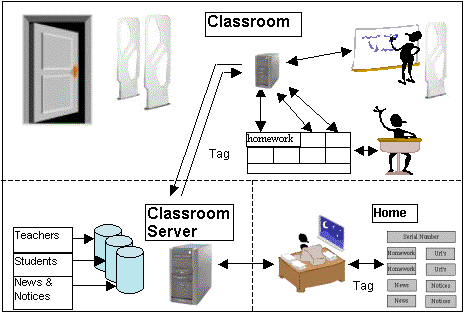
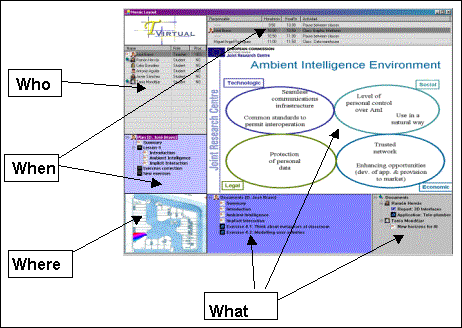
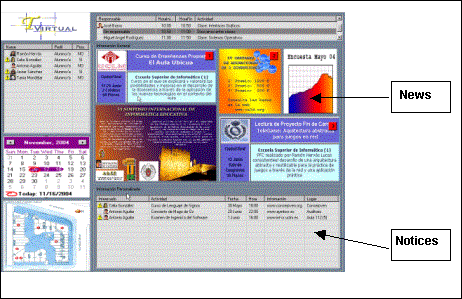
This is an appropriate moment to recall the definition given by A. K. Dey: "Context is any information that can be used to characterize the situation of an entity. An entity is a person, place, or object that is considered relevant to the interaction between a user and an application, including the user and application themselves." [Dey, 01]. Schilit defines context-aware computing to be how "software adapts according to the location of use, the collection of nearby people, hosts, and accessible devices, as well as to changes to such things over time". [Schilit, 94] Dey considers that a system is context-aware if it uses context to provide relevant information and/or services to the user, where relevancy depends on the user's tasks. When thinking about the aspect of the classroom context, the profiles (students and teachers), are in "who", the schedule in "when", the classroom in "where", the tasks (visualization services and homework control) in "what" and, lastly, the natural interaction in "why". We have focused these context aspects on identification [Bravo, 03, 04]. For this reason we are placing the concepts strategically in order to obtain user services, as Figure 3 and Table 1 show. Other services appear in this figure. These are embedded in the identification process itself and are presence, location or access controls. Thus the "what" (services) can be obtained through the following function, combining "who", "when" and "where". ID (profile, schedule, context) -> Service Table 1: Identification-based services Page 1498 Figure 3: The context concepts in the classroom through identification. In the following sections we detail those services that the identification process provides in our classroom context. 3.1 Identity awarenessThis is the basic process that is carried out by readers placed strategically in the school center. In our case there are readers located on every classroom door. These will capture the information necessary to know who is inside (or there may even be two readers to avoid in/out ambiguities). Through each reading, the system obtains users' data from a database, determining each profile and deciding the system's behavior. In addition, the database contains data about teachers' and students' needs, offering adapted information. Other services such as control of class attendance are important at secondary education level. Here, the teachers are concerned about non-attendance to school. Page 1499 Figure 4: Identification process architecture. 3.2 Location awarenessThe system knows about the people in the room and the proximity of everyone to the board (projection screen) (Fig. 4). To do this, only an additional antenna near the board is necessary. If the teacher approaches the board, the information will be shown automatically for each subject (presentations, examples, url's, etc.). If it is the student who approaches the board, the information concerning him/her will be shown, for example the solution to their homework. In both cases the system responds without the users' explicit interaction. Lastly, annotations and the teacher's corrections are stored in the database -they will be placed in the student's label when this individual leaves the classroom. Later, at home, the student accesses homework via a personal reader. 3.3 Time awarenessThe system knows about the tasks that will be developed in the classroom at all times. It knows if it is time for class, rest or any other type of activity. In addition, it has stored the school calendar, so it is able to differentiate between the time for regular classes, examination periods or holidays. This time aspect is important, but it is also complemented with the other aspects mentioned above; profile and location. By knowing each user's timetable (class schedule, meetings, etc.) the contextual information becomes remarkably rich. Page 1500 3.4 Task awarenessThe task knowledge desired can be acquired through the users' explicit interaction extracted from the concepts mentioned previously (time, location and identification). We believe that identification is, in fact, the action which is the most significant in anticipating the users and in offering them all the implicitly required services. It is obvious that one of the fundamental tasks in the classroom is the presentation of information (Visualization). In our ubiquitous classroom approach, this presentation is spontaneously shown through user identification. Figure 5: Teacher's Profile board. Figure 5 shows the information and services available in a typical scenario in the classroom. It includes the teacher's profile information. The presentation, attendance, school calendar (schedule), teacher's plan, classroom location, documentation and exercises can be observed (what, who, when & where). In the visualization service the context aspects are represented. The corresponding scenario is the following one: When the teacher arrives at the classroom, the reader and the antenna placed near the door read his/her tag. The computer immediately changes the schedule on the top of the board, showing that the class is about to begin. In the top left-hand corner, there is also a list of the learners who are present in the classroom. Below that, the teacher's plan is activated. This plan indicates the different tasks the teacher aims to carry out in the lesson. Finally, the system shows the presentation of the unit being explained (the largest part of the board)- this is the first task of the aforementioned plan. Below that, all the information relative to this unit- url's, proposed problems, activities, etc. is shown. Page 1501 In Figure 6, the student's profile is displayed in the time between classes. In this, general and individual information is presented, with news and notices adapted to everyone. The first type depends on a general profile- for instance, students at the same level. The second deals with individual information and is shown when each student approaches the board (proximity). Figure 6: Student Profile board. 3.5 The "way" aspect: Implicit InteractionThis concept is perfectly justified in our identification process. Through RFID technology and situations of the type in/out of the classroom or proximity to the board we achieve the principle of iHCI. In this, the input to the computer are the daily activities in the real world. 4 ConclusionsThis has been a first approach to the ubiquitous classroom through the identification process with RFID technology, attempting to follow the principles that the interaction paradigm proposes. We consider it important to establish mechanisms to facilitate services to the user in a natural way. In this sense, the labels fulfill this objective perfectly, since the only necessary requirement is for the users to be wearing them at the time of identification. We believe that the adaptation of new devices is necessary for the further enriching of the classroom. Page 1502 This will imply the automation of daily activities, resulting in benefits for both teachers and students. In this direction, we are trying to improve our system towards the control of actions such as displaying slides, changing activities in the plan, or ending the class. To do this, we are working on a prototype sensor subsystem which allows us to detect the movement of a hand near the board at different distances from the bottom edge of this surface. Acknowledgements This work has been financed by a 2005-2006 SERVIDOR project from Junta de Comunidades de Castilla-La Mancha. References[Abowd, 00] Abowd, G.D. & Mynatt, E.D. (2000). "Charting Past, Present and Future Research in Ubiquitous Computing". ACM Transaction on Computer Human Interactions, Vol. 7, 1 Pag. 29-58. [Beigl, 01] Michael Beigl, Hans-W. Gellersen and Albrecht Schmidt (2001). "MediaCups: Experience with Design and Use of Computer-Augmented Everyday Artefacts" Computer Networks, Special Issue on Pervasive Computing, Elsevier. Vol. 35, No. 4, March 2001, Elsevier, p. 401-409. [Bravo, 03] J. Bravo, R. Hervás, Sánchez, I. & Crespo, A. (2003). "Location-Based Services: Context, Profiles, Objects and Time". Internal Report, Castilla-La Mancha University. [Bravo, 04] José Bravo, Ramón Hervás, Inocente Sánchez, Agustin Crespo. "Servicios por identificación en el aula ubicua". In Avances en Informática Educativa. Juan Manuel Sánchez et al. (Eds.). Servicio de Publicaciones - Universidad de Extremadura. ISBN84-7723-654-2. [Brooks, 03] Kevin Brooks (2003). "The Context Quintet: narrative elements applied to Context Awareness". In Human Computer Interaction International Proceedings, 2003, (Crete, Greece) by Erlbaum Associates, Inc. [Cox, 03] Cox, D., Kindratenko, V. & Pointer, D.(2003) "IntelliBadge:Towards Providing Location-Aware Value-Added Services at Academia Conferences. A.K.Dey et al (Eds.): Ubicomp 2003, LNCS. Springer. [Dey, 01] Dey, A. (2001). "Understanding and Using Context". Personal and Ubiquitous Computing 5(1), pp. 4-7. [Harrison, 98] Harrison, B.L. et al. (1998). "Squeeze me, hold me, tilt, me! An exploration of manipulative user interfaces". In Proceedings of the ACM Conference on Human Factors in Computing Systems (CHI'98). Los Angeles, CA. [Ishii, 97] Ishii, H & Ullmer, B. (1997). "Tangible bits: Towards seamless interfaces betwen people, bits and atoms". In Proceedings of the ACM Conference on Human Factors in Computing Systems (CHI'97). Atlanta. [Schilit, 94] Schilit, B., Adams, N. & Want, R. (1994). "Context-Aware Computing Applications". In Proceedings of the Workshop on Mobile Computing Systems and Applications, Santa Cruz, CA, December 1994. Pages 85-90. IEEE Computer Society. [Schmidt, 00] Schmidt, A. (2000). "Implicit Human Computer Interaction Through Context". Personal Technologies Volume 4(2&3) 191-199. Page 1503 [Schmidt, 05] Schmidt, A. (2005). "Interactive Context-Aware Systems. Intering with Ambient Intelligence". In Ambient Intelligence. G. Riva, F. Vatalaro, F. Davide & M. Alcañiz (Eds.). [Want, 92] Want, R. & Hopper, A. (1992). "The Active Badge Location System". ACM Transactions on Information Systems, 10(1):91-102, Jan 1992. [Weiser, 91] Weiser, M. The computer for the twenty-first century. Scientific American, September 1991, 94-104 (1991). [Weiser, 98] Weiser, M. (1998). "The future of Ubiquitous Computing on Campus". Communications of the ACM, 41-1, January 1998/Vol. 41, No. 1. Page 1504 |
|||||||||||||