| Submission Procedure |
LAN Access Over ISDN
(Graz University of Technology, Austria fpucher@iaik.tu-graz.ac.at) (Graz University of Technology, Austria hleitold@iaik.tu-graz.ac.at) (Graz University of Technology, Austria rposch@iaik.tu-graz.ac.at) Abstract: This paper describes local area network (LAN) access using public wide area data networks and problems that arise when using integrated services digital network (ISDN) technology [Stallings 90] [Thachenkary 93]. To date mainly modem connections at serial lines with a terminal port have been the standard remote access technique. With ISDN it is foreseen that these modem lines will be replaced rather soon. This is mainly due to the fact that ISDN offers a more adequate bandwidth and is much more consistent from the point of view of access and embedding. This paper demonstrates in the main section a router-based solution for enhanced call management. One of the main advantages is the separation of the strategic module which defines the behavior and thus allows for a number of active connections exceeding the number of ports. It also addresses traffic and access control in the network environment. Category: C.2.5 1 Introduction
Remote LAN access is an important application of public wide area data networks. For data communication, commercial use of modems has been popular for more than a decade. The use of modems has increased substantially corresponding with the increase in popularity of personal computers (PCs) and Fax machines. There are more than 15 million dial up modems in the world. These modems operate at line rates ranging from 300 to 28.8 kb/s. At a capacity of 128 kb/s, the ISDN basic rate interface (BRI) offers an enhanced alternative for many user applications. This is because of the following: * The need for higher bandwidth due to the increasing popularity of graphical computing and multimedia interactive services. Users have Page 20 become accustomed to graphical user interfaces on their PCs and also prefer it for remote applications. * Multiple vendors have intruduced ISDN BRI cards for PCs that are available at modem price levels, and which are compatible with standard modems such as V.32 bis. * Service availability and connectivity has increased to serve more than 70 percent of the population in many regions of the world. ISDN BRI is also emerging as an attractive supplement for private line connections: interconnection of LANs, connection of point-of-sale (POS) terminals to servers, and connection of clusters of user terminals to servers. ISDN BRI can be used to supplement private lines during peak traffic periods, thereby reducing line capacity. This is also referred to as bandwidth on demand [BONDING 92]. A further benefit of a supplementary ISDN connection is increased reliability of the connection in case of line failure. In addition, corporate private networks (PN), where private branch exchanges (PBX) are connected through leased lines, are very popular in Europe and North America. Virtual private networks (VPNs) offer an attractive alternative for some configurations where private lines are not economical. In this case, physical facilities are not dedicated to all of the endpoints. Instead, network resources are allocated on demand to meet the needs of end-user applications. In effect, the customer network becomes a logical partition of the much larger public network. The user application "virtually" has a constant availability of connections, where the public network laid the foundations with the allocation of shared resources on demand. While not necessarily breaking speed and performance records ISDN does offer universal connectivity with sophisticated signaling and control mechanisms which makes it a well-defined, natural progression from PSTN. Moreover, use of ISDN for LAN access is still an area at the development stage and needs sophisticated traffic and access control as well as many more features which have not been evident with modem lines. This paper provides an up-to-date account of available access possibilities, how ISDN BRIs can be connected directly into LANs, and presents a router-based solution for an ISDN primary rate interface (PRI) with enhanced call management. What is known as a strategic module, between the data link- and the network layer, controls the connection establishment and maintenance. This allows for a number of active connections that exceeds the number of ports. It also addresses the issue of traffic- and access control in the network environment, which can be controlled through a network management station and a monitor by the simple network management protocol (SNMP) [Davin et al. 88]. This low cost solution is proposed as an adequate alternative to the remote access service (RAS) [Awuah, Lazar 94] of Microsoft. It has many advantages, if the number of users increases or if LAN-to- Page 21 LAN access has to be provided. Due to the open interface, user specific extensions can be attached and in this way achieving greater flexibility. The paper is structured as follows: [Section 2] gives a brief overview of the network used. [Section 3] describes the current possibilities for embedding ISDN into a LAN. In [Section 4] the router-based solution and the subnetworking for the PRI is shown. [Section 5] and [Section 6] describe the flexibility due to the ability of modular extending to meet enhanced requirements. [Section 7] concludes the paper. 2 Departmental LAN
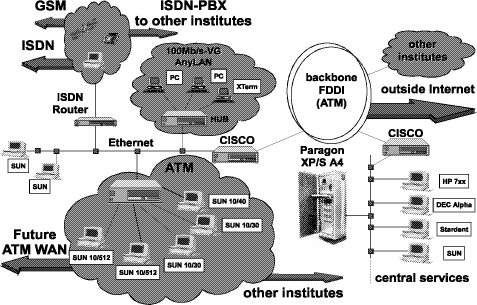
[Fig. 1] is a schematic picture of the configuration, showing the present university system and location of central university facilities. To some extent experimental technologies such as asynchronous transfer mode (ATM) and ISDN still fall within the institute,s responsibility. The number of hosts in the various parts is schematic. Although many protocols like Decnet, Novell, etc. are used simultaneously, the transmission control protocol/internet protocol (TCP/IP) family is used most often. As can be seen from [Fig. 1] the mixture of topologies and media is spreading to all departments. Therefore, the addressing scheme has to cope with two contradicting paradigms: Firstly, one department should look to the outside world as one subnet or domain. Secondly, each medium should be one subnet for performance and managerial reasons. Moreover, with mobile stations the subnet structure might even be required to be dynamic.
Page 22 For outside connections ISDN BRI/PRI links are embedded in the institute,s network. In this environment questions of line usage, movability of the remote stations, variability of charging, throughput, security functions, data encryption, and compression are studied. Other experiments with this network include network management with SNMP, embedding of security, and scheduling policies to provide access to the network to more users when channels are not readily available. 3 The Embedding of ISDN into LANs
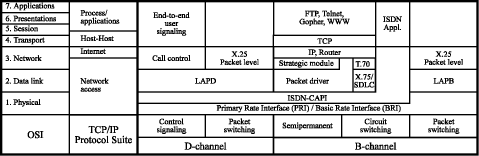
For interaction between ISDN users and a network and for interaction between two ISDN users, ISDN access can be controlled through a driver architecture within the open systems interconnection (OSI) framework [Stallings 94]. [Fig. 2] shows the relationship between OSI, TCP/IP protocol suite, and ISDN. As a network, ISDN is essentially unconcerned with user layers 4 through 7, which are end-to-end layers employed by the user for exchange of information. Network access is concerned only with layers 1 through 3. The physical interface for BRI and PRI corresponds to OSI layer 1, where B- and D-channels are multiplexed over the same physical interface. Above layer 1, the protocol structure for the two channels differ. For the D-channel, a new data link layer standard, link access procedure for the D-channel (LAPD), has been defined. This standard is based on high-level data link control (HDLC) [ISO 76], modified to meet ISDN requirements. The D-channel part in [Fig. 2] supports an exchange of service primitives, which are used to establish, maintain, and terminate connections on B-channels. The D-channel can also support X.25 packet-switched data transmission, which is transmitted in LAPD frames. The X.25 level 3 protocol is used to establish virtual circuits on the D-channel to other users and to exchange packetized data. The B-channel part in [Fig. 2] enables voice, data, and image communication. For data communication the B-channel can be used for circuit switching, semipermanent circuits, and packet switching. For circuit switching, a circuit is established on demand on the B-channel and provides a transparent data path between end-users. A semipermanent circuit is a B-channel circuit that is established by prior agreement between the connected end-users and the network. With either a circuit-switched connection or a semipermanent circuit, the connected stations seem to have a direct, full-duplex link with one another. They are free to use their own formats, protocols, and frame synchronization. In the case of packet switching, a circuit-switched connection is established on a B-channel between the user and a packet-switched node using the D-channel control protocol. To provide access to ISDN for applications independent of the underlying network and the ISDN adapter cards used, a common ISDN application interface (ISDN-CAPI) [CAPI 92] was defined by different vendors. The ISDN-CAPI provides a Page 23 standardized interface for any number of applications to any number of ISDN drivers and controllers. This interface offers unique access to the different ISDN services such as data, voice, fax, video, and telephony. Applications can use different protocols at different levels, where the ISDN-CAPI provides a selection mechanism supporting this. For LAN integration, optimal line usage and flexibility, circuit switched connection and the Ethernet addressing scheme is used. The protocol stack, where a packet driver can be used by a wide variety of card manufacturers is given in [Fig. 2] (right).
Packet drivers [VanBokkelen 89] provide a simple, commonly used programming interface that allows multiple applications to share a network interface at the data link level. The packet drivers demultiplex incoming packets amongst the applications, by using the network,s media standard type or service access point field. The packet driver provides calls to initiate access to a specific packet type, to end access to it, to send a packet, to get statistics on the network interface and to get information about the interface. Applications which use the packet driver can also run on new network hardware (like ISDN) of the same class without having to be modified; only a new packet driver needs to be supplied. The network media is identified by a number-the class of the interface. However for some classes, packet drivers do exist. The packet driver PAPI [Friede 93] was developed for the SLIP class [Romkey 88], SUNLink [SUN 93] uses PPP [Simpson 92] for communication between two SUN-WS. However, the most flexible class seems to be the Ethernet class 1 packet driver, which supports the Ethernet frame. One class 1 packet driver is ISPA [Hanewinkel 95] which also supports SLIP, PPP, and the Cisco HDLC frame format. Another class 1 packet driver is ISDNPKT [Frackowiak, Heinen 92], a commercial product from INS. Access to the Ethernet LAN through DOS based versions can be provided by means of routers and bridges. With current packet drivers and available routers, remote access can only be established for a limited number of users. A more sophisticated approach for allowing access to more users is shown in [Section 4]. Page 24 4 A Router Based Solution for 30 B-Channels
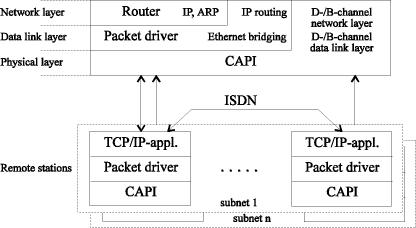
As Ethernet class packet drivers are supported by the multitude of available network software for PCs, this packet driver class has been chosen to give maximum flexibility to the remote LAN access. However, the available commercial and non commercial solutions such as RAS, SunLink, PAPI or ISDNPKT differ in this respect, as PPP or SLIP is used. As there is no full interoperability between the products of different vendors, the decision has been made to allow the use of a variety of available routers and bridges instead of achieving full interoperability with one product. Mainly due to the increased system load caused by enhanced requirements like encryption and compression, flexibility in selecting the router software is emphasized, when a PRI with the ability for 30 simultaneous connections has to be dealt with. A router connects networks at the network layer, terminates the media access control (MAC) layers of each connected LAN, and permits translation between different address domains. ISDN-CAPI, the interface used, terminates the network layer of the ISDN access. As the ISDN packet driver has to transform the MAC layer termination of the router software to the network layer termination of the underlying PSTN, OSI embedding is demaged. To deal with this problem, the ISDN-Ethernet packet driver has to support a transparent MAC layer access to the router software and, therefore, perform routing functions itself. As the packet driver has to assign Ethernet packets to certain remote stations, the packet driver's routing functions leads to two assignment decisions: * Broadcast packets: When circuit switched lines are used in a PSTN, broadcasting these packets create additional costs. Thus, during the address resolution protocol (ARP) [Plummer 82] sequence the packet driver evaluates the IP address, to determine the requested station in case of an ARP request. The unique Ethernet MAC address delivered with the corresponding ARP response is assigned to the ISDN subscriber. This is called the IP-routing function of the packet driver. * Non braodcast packets: The Ethernet specification demands unique MAC addresses to perform logical point-to-point communication between two nodes in a subnet. This fact is used to assign a non-broadcast packet to a requested remote station evaluating the destination MAC address. As the assignment of the packets is performed at the MAC layer, this is called Ethernet-bridging function of the packet driver. To achieve the level of demanded MAC address uniqueness, each packet driver computes its MAC address using the unique ISDN subscriber number. The routing scheme is limited to the ARP sequence, as IP addresses are only evaluated when IP-routing is performed. Because the packet driver,s routing functions can unequivocally determine the ISDN subscriber to be addressed, the packet driver can decide, whether or not the packet has to be sent to a station belonging to the same subnet, or whether an ISDN router has to be addressed. Page 25 Therefore, all possible ISDN connections are kept in a table which consists of the ISDN subscriber number, its MAC address, IP address and other status information. The router-based solution for a network consisting of several subnets and the OSI layering of the ISDN packet driver, capable of integrated IP-routing and Ethernet-bridging functions is presented in [Fig. 3].
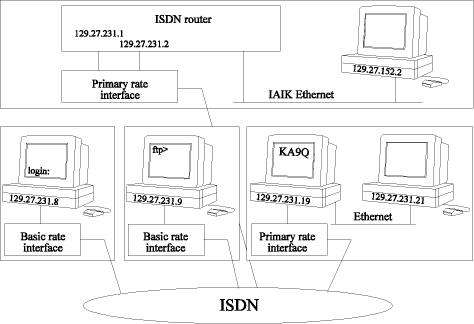
The scheme allows each ISDN subnet to be considered as one physical network. A PC-based router software performs the logical connection between the Ethernet LAN and ISDN. In [Fig. 4] the LAN-ISDN topology is shown. The figure shows an ISDN-PRI router handling another PRI and two BRIs using two subnetworks. The subnetworks and the end systems with its internet addresses are shown. End systems can be connected to ISDN using the PRI or BRI. ISDN channels are established automatically on demand. The datagrams are transmitted and time-outs are set in such a way, so that after a certain period ofinactivity, the channels are closed down. The system described in this section meets the necessary requirements of transparent LAN access using the TCP/IP standard. However, the utilization of public telecommunication networks like ISDN, results in requirements exceeding the capabilities of the system presented. The following [Section 5] introduces an enhanced system which allows more users access to the LAN than ISDN lines available. Page 26
5 Meeting Enhanced Requirements
The router-based solution described in the previous [Section 4] is limited in its flexibility. Since using ISDN to access LANs has to be viewed within the context ofa wide area network (WAN), several objectives have to be achieved: (1) Line usage: A remote connection should retain the line for a minimum amount of time (or line cost). Even if the charging policy by the service provider discriminate very much against short local connections, due to the de facto minimum charges as they frequently do, connection management pays off for any communication. (2) Movability of remote stations: The location of the next packet in the module, even of the same session would ideally be at a different point chosen arbitrarily. Portable computers retaining a logical connection while traveling around is just one example. This requires the separation of the physical connection from the logical LAN connection. (3) Logical ports: It would be desirable to share k ports amongst n users, where m of the n users are active and have a logical connection. Thereby both n and m could be reasonably larger than k. This feature seems to be most important for flexibility. (4) Variability of charging: The connection should be charged either to the caller or to the station called, depending on the users attributes and the systems charging policies. Page 27 (5) Throughput: The allocation of channels possibly grouped together to form a link should be dynamic and should depend on the users policy and on the load on the link. (6) Security functions: Even if ISDN allows caller identification, the security conditions required are not sufficient. Highly dynamic and mobile behavior demands enhanced security. Passwords are generally assumed to be lacking in security. Therefore, the access module must provide an integrated security module. (7) Data encryption and compression: For trusted connections, encryption modules should be attached, so that all information is encrypted as it is sent. This mechanism provides protection against wiretapping as well as access by unauthorized users. For technical reasons, compression mechanisms to get a higher throughput could be combined. (8) Scheduling of incoming calls/signaling: This is the major drawback associated with the router-based solutions available. Efficient usage of ports is one of the major problems of remote access. With short setup times ISDN makes it possible to introduce port management and scheduling independent of the logical connection. (9) Accounting: It may be necessary to log the ISDN activities to facilitate charging the user's ISDN-LAN access. (10) Logging: Both establishing ISDN lines and the transferring data should be accessible due to possible network security attacks. (11) Network statistics: Statistics of network usage, transfer rates and transmission or line setup errors are needed to optimize the remote LAN access. To support flexibility, strategic functions can be attached over a strategic interface to the packet driver. These functions are used to manage the cooperation between the packet driver and the strategic module which performs the execution of user-specific requirements. The interface is located between the packet driver and the strategic module and consists of three main parts: * Packet driver interrupt: Additional functions have been defined to prepare the packet driver for cooperation with the strategic module and to gain access to the current packet driver configuration. * Parameter adjustment: Accessing the data structures kept in the packet driver's memory, allows direct adjustments to the logical and physical connections. * Up-call function: The packet driver indicates ISDN activities such as setting up or closing a physical connection using an up-call function. Moreover, the activities corresponding to the logical connection, such as which packets to transmit, can be requested by the strategic module. The introduction and separation of the strategic module is seen as the main advantage of the implemented packet driver. To give an example of the strategic module, the actions necessary for managing a number n of users exceeding the Page 28 number k of available B-channels are described. Assigning the remote station, there are two possibilities: * Incoming call management: In case of an incoming call, the packet driver compares the caller's ISDN subscriber number with the one configured in the table. * Integrated routing and bridging: The integrated IP-routing and Ethernet-bridging functions allow the assignment of a packet to be transmitted to the remote station which is addressed using the IP- and Ethernet MAC- addresses of the packet.
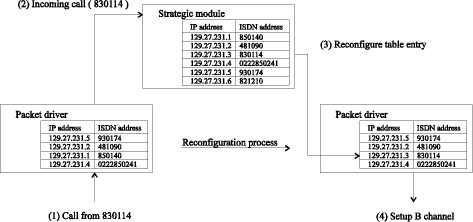
Due to the ability to manage n logical ports simultaneously, the packet driver has a partial scope of the entire network. It has been shown in [Section 4], that the packet driver holds a table of size k, which is used to assign the packets to the ISDN lines. If an activity refers to a remote station, that is beyond the packet driver's scope, both the incoming call management and the integrated IP-routing and Ethernet-bridging functions fail to assign the activity to a certain table entry. The packet driver indicates this, and requests the support of the strategic module which has the scope for the entire network. The strategic module is passed the parameters necessary to process the request (caller address or the packet to transmit). The routing necessary to assign the requested remote station has to be done by the strategic module, which decides on the reconfiguration of the packet driver. Therefore, it replaces an entry of the packet driver's table with the parameters needed. The partial scope of the packet driver has changed dynamically. After the replacement of the table entry, the packet driver carries out the new entry using its integrated IP-routing and Ethernet-bridging function. [Fig. 5] shows the four steps needed to reconfigure the packet driver in case of an incoming call. The packet driver handles k=4 B-channels (two BRIs). The network managed by the strategic module consists of n=6 remote stations. In this way the crucial steps needed to reconfigure the packet driver are carried out, provided that the number of B-channels needed equals or exceeds the number Page 29 available. Different strategies of replacing the packet driver's table entries have to be evaluated in order to meet the possible demands of different situations (this led to the name strategic module). Some approaches to managing the packet driver's partial network scope used by the strategic module might be: * Priority scheme: Entry with the lowest priority is replaced. * Inactive time: Strategic module searches for an entry which has been inactive for the longest period of time. * Channel reduction: If B-channels are grouped to increase the throughput, then these B-channels are assigned to other users to increase the number of possible logical ports. * Alternative routes: The logical connection might be routed to another ISDN router (backup system) to meet system load peaks. * Combined strategies: The strategies described above may be used together. For example, several users might be grouped together as a priority class. Every priority class is assigned a fixed number of B-channels which are distributed using the channel reduction scheme. The example in [Fig. 5] presented the evolution of the router-based solution for 30 B-channels (described in [Section 4]) to a method that allows for dynamic reconfiguration of the packet driver. However, in that case the strategic module is configured statically, so the solutions do not reach maximum flexibility. The following [Section 6] describes the possibility of a dynamic reconfiguration of the strategic module. 6 Remote Maintenance and Management
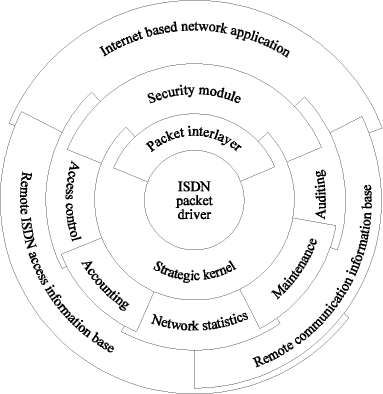
A solution to the remote LAN access using ISDN was described in [Section 4] and [Section 5]. It has been shown that the network application has the scope of an attached Ethernet, although the remote LAN access does not achieve the same performance because of a lower transfer rate and higher ISDN setup times. The solution presented allows adjustment to user-specific requirements using a strategic module. However, in the case of networks consisting of a high number of remote stations or several ISDN routers, the need for easing network management and maintenance is greater. This, together with the enhanced requirements described in [Section 5], demands for a modular design of the strategic module, as easy replacement or maintenance of several modules becomes necessary. To allow for distribution of maintenance- and management tasks, the strategic module has to be divided. The packet driver is encapsulated in a module consisting of a strategic kernel and a packet interlayer. The packet interlayer allows access to any transmitted packet and controls communication on the logical links. The strategic kernel manages the strategic interface activities. Its main function is the distribution of these activities, as they might be needed by different modules. For example, the indication of establishing an ISDN line is needed by the accounting Page 30 module as well as by the access control module and the security module. The modules surrounding the strategic kernel and the packet interlayer process the necessary requirements and are installed on demand. These modules form the local envelope for the strategic module. This envelope can be accessed by distributed information base systems to perform management functions. SNMP is used as access protocol. [Fig. 6] gives an overview ofa modular designed strategic module.
The modular design allows the use of implemented modules separately or a combination of some of them. It also encourages efforts to take further steps in the network management area. Thus a flexible way of adjusting the remote LAN access to meet different requirements has been shown. 7 Conclusion
The rapid evolution of ISDN has created conditions for the development of systems that use its facilities efficiently. The 64 kb/s circuit switched channel is the most common barrier service by carriers offering good opportunities for LAN access through ISDN. The router based solution presented in this paper for a PRI with Page 31 30 B-channels on the router-side and a BRI or PRI on the user-side tries to schedule all incoming calls in such a way that each user gains access to the LAN. In addition to the use of a PRI for remote access, the router can provide access to an Ethernet LAN for more remote stations than channels available. To do this, several strategies have been implemented which are controlled in a separate module, the strategic module. The strategic module can also provide for security in communication as well as authentication and access restrictions. For future requirements different ways of signaling can be used to speed up the network access, such as the ISDN user-user signaling system (USS 1) or the packet switched connection over the D-channel; both can be used to deliver status information. Comprehensive performance evaluations have been made to allow comparison of different solutions. They proved, that the transfer rate is not limited by the packet driver, as the theoretical transfer rate of 64 kb/s per established B-channel is possible. However, depending on the quality of the network software used, losses in transfer rate may occur. The first transmitted packet is delayed, because of the time needed to establish a B-channel. This setup time depends on the number of switching points that are required to establish the connection and has achieved values ranging from between 0.4 and 1.0 seconds. One of the most important considerations in this work is the independence of the card manufacturers and the use of compatible hardware with public domain software for reasons of cost. This factor, along with the separation of the strategic module which defines the behavior, and thus allows for a number of active connections exceeding the number of ports, means that a flexible way of adjusting the remote ISDN-LAN access to different requirements is possible. References
[Awuah, Lazar 94] Awuah, P., Lazar, D.: [BONDING 92] Bonding: "Interoperability Requirements for Nx56/64 kb/s Calls, Version 1.0"; Bonding Consortium, September 1992. [CAPI 92] Common-ISDN-API Spezifikation, Version 1.1, Profile A (mit Ergaenzungen), l992. [Davin et al. 88] Davin, J., Case, J., Fedor M., Schoffstall, M.: "A Simple Network Management Protocol (SNMP)"; RFC 1067, USC/Information Sciences Institute, August 1988. [Frackowiak, Heinen 92] Frackowiak, A., Heinen, W.: "ISDNPKT documentation"; Inter Networking Systems (INS), Commercial Link Systems (CNS), 1992.
Page 32 [Friede 93] Friede, D.: "PAPI 0.20: SLIP class packet driver"; ftp://ftp.germany.eu.net/pub.networking/, 1993. [Hanewinkel 95] Hanewinkel, H.: "ISPA 3.34: An ISDN packet driver"; ftp://ftp.biochem.mpg.de/pc/isdn/, 1995. [ISO 76] ISO, DIS 3309.2 and DIS 4335: "High-Level Data Link Control (HDLC)"; l976. [Plummer 82] Plummer, D. C.: "An Ethernet Address Resolution Protocol" ; RFC 826, USC/Information Sciences Institute, November 1982. [Romkey 88] Romkey, J.: "A Nonstandard for Transmission of IP Datagrams over Serial Lines: SLIP" , RFC 1055, USC/Information Sciences Institute, June l988. [Simpson 92] Simpson, W.: "Point-to-Point Protocol (PPP)"; gRFC 1331, USC/Information Sciences Institute, May 1992. [Stallings 90] Stallings, W.: "ISDN: An Introduction"; Macmillan Publishing Company, Canada 1990. [Stallings 94] Sta11ings, W.: "Data and Computer Communications - 4th ed."; Macmillan Publishing Company, New York 1994. [SUN 93] SUN Microsystems, Inc.: "SunLink ISDN 1.0 Software Reference Manual", 1993. [Thachenkary 93] Thachenkary, C. S.: "Integrated Service Digital Network (ISDN): six case study assessments of a commercial implementation"; Computer Networks and ISDN Systems, North-Holland, 25, 8 (1993), 921-932. [VanBokkelen 89] VanBokkelen, J. B.: "Packet Driver Specification, Revision 1.09"; FTP Software, Inc., ftp://ftp.ftp.com/Pub/packetd/, 1989.
Page 33
|
|||||||||||||||||
 Server 3.5: Remote Access Service (RAS), Whitepaper, September 1994.
Server 3.5: Remote Access Service (RAS), Whitepaper, September 1994.